The Case Management Platform that will make your security job easier
What was once a humble open-source project is now trusted by hundreds of SOC, CERT, CSIRT and other teams worldwide. The current version of the platform, TheHive 5, is our most advanced one ever, thanks to years of innovation, development, and invaluable real-world input from our users and community.
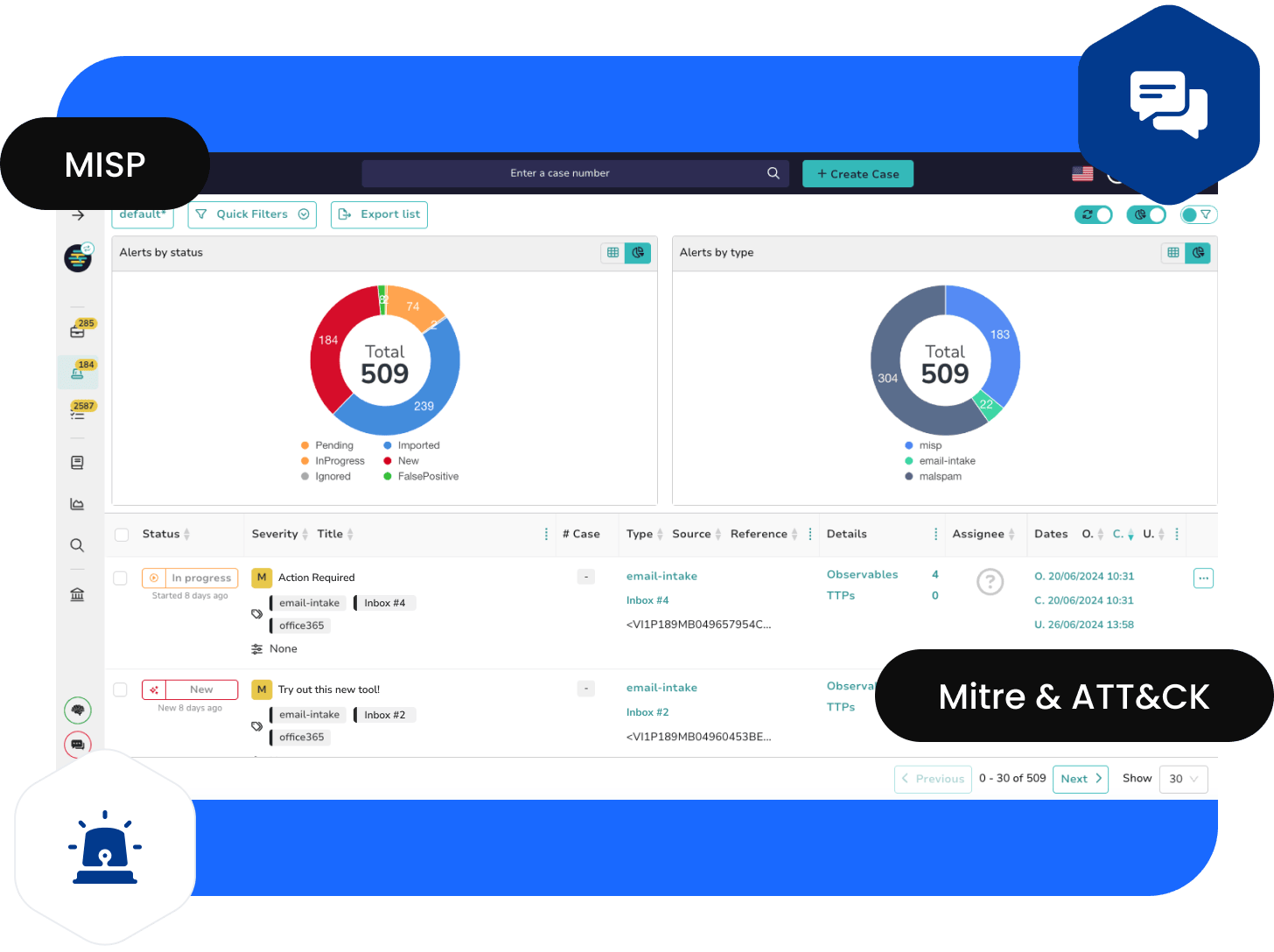
Get complete visibility of all incidents and reduce alert fatigue.
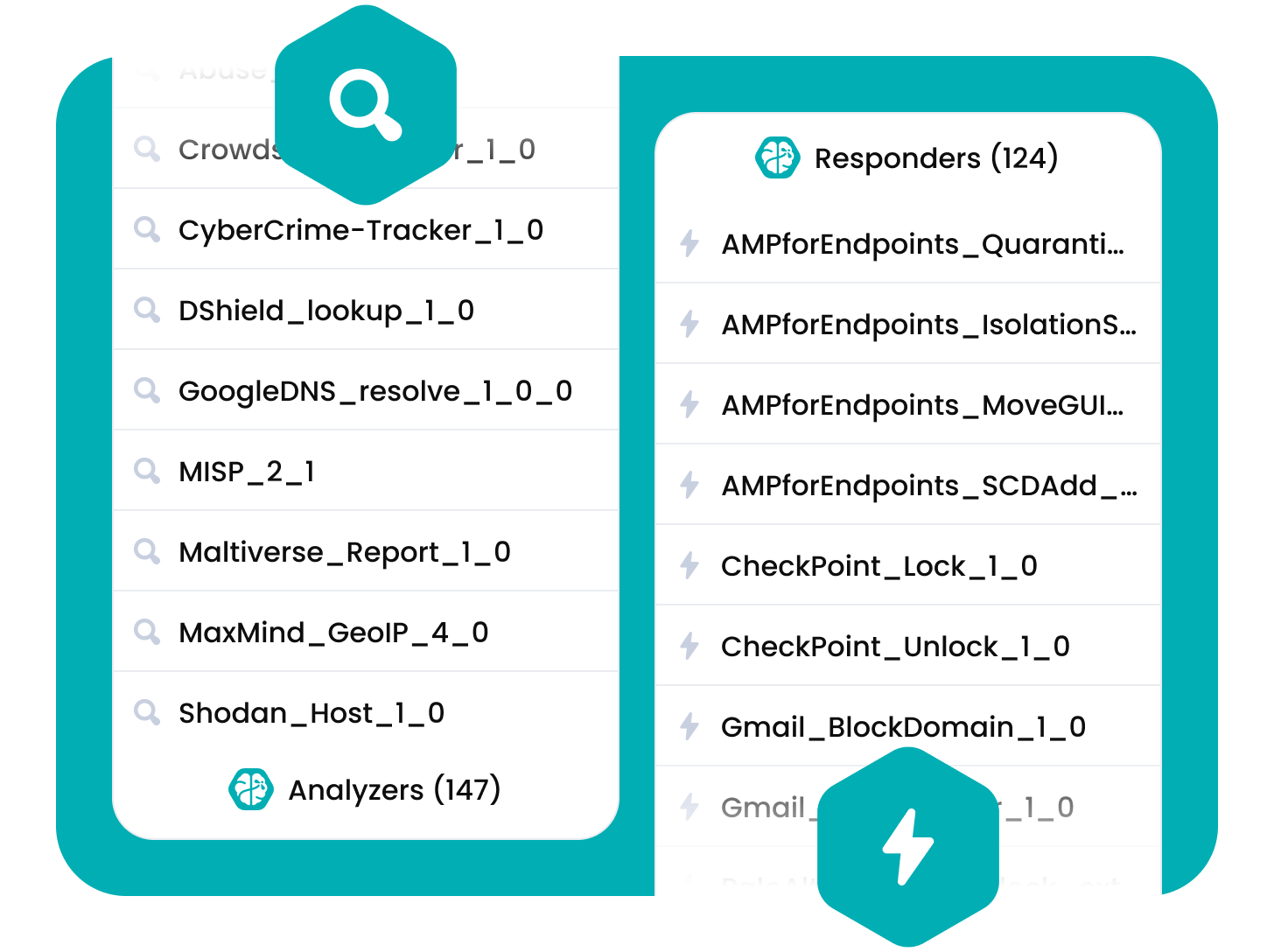
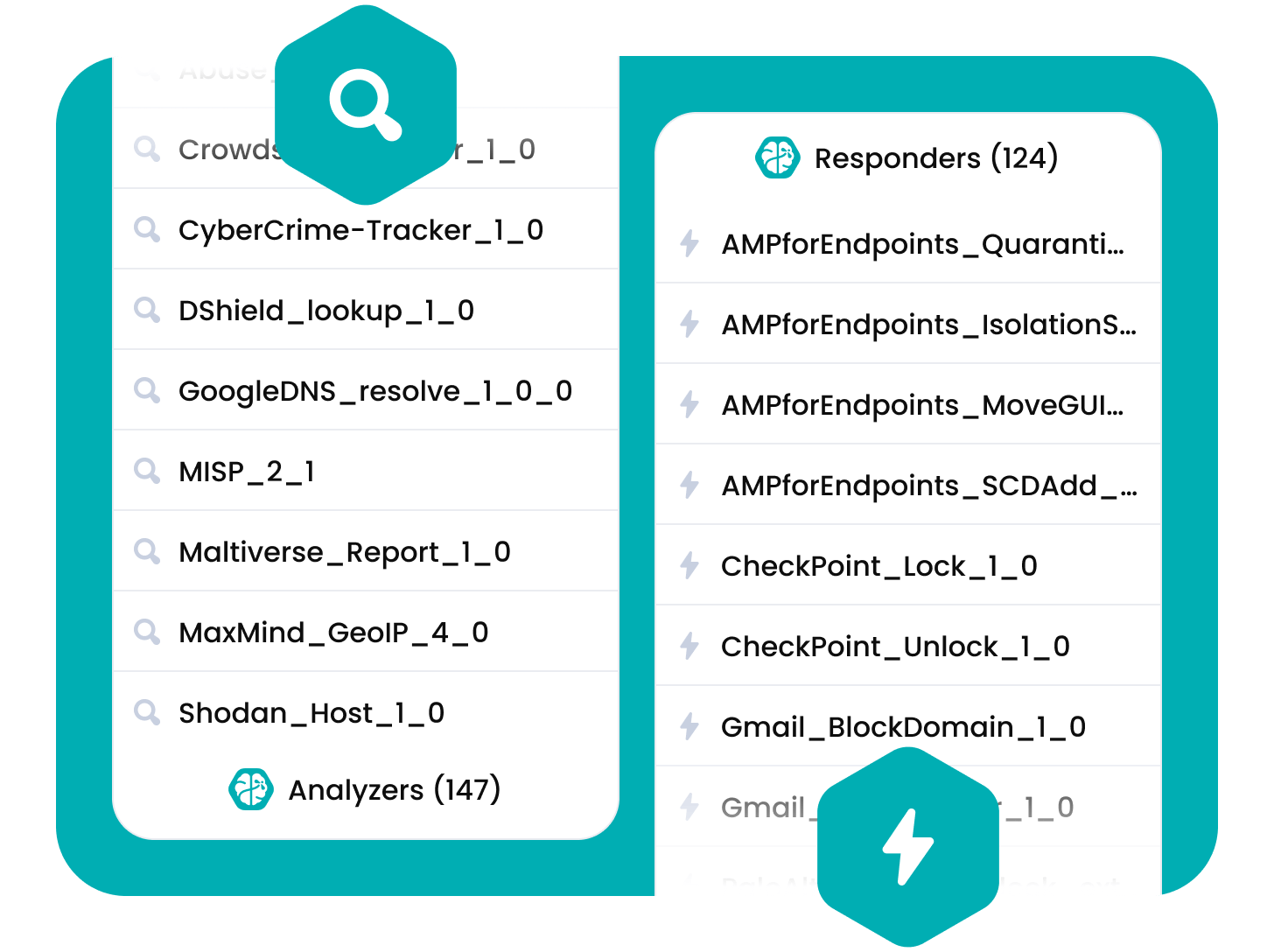
Automate incident response’s tedious steps, saving time to concentrate on what matters.
Customize without limits: choose where to receive alerts, what to integrate with, how to filter criteria, and more.
Collaborate in real time, investigating incidents together with other teams and reaching resolutions faster.
100% visibility
Get complete visibility of all incidents and reduce alert fatigue.
Automation
Automate incident response’s tedious steps, saving time to concentrate on what matters.
Customization
Customize without limits: choose where to receive alerts, what to integrate with, how to filter criteria, and more.
Collaboration
Collaborate in real time, investigating incidents together with other teams and reaching resolutions faster.